To request certificates from Forefront TMG ports need to be opened to allow access from Forefront TMG to the Certificate Authority. This is a known situation and there is a blog post at ISA Server on how to accomplish this.
But if the CA is a Windows Server Core installation, it is a little more tricky to configure the CA to use a static port. It is not possible to remote manage the DCOM part of the CA using the MMC Component Services Add-in.
You can do this directly through the registry using regedit on the Server Core installation.
- Find the Application ID GUID of the Certificate Server Request component.
- Update the key to use a fixed port.
- Restart the Certificate Service.
Find the Application ID GUID
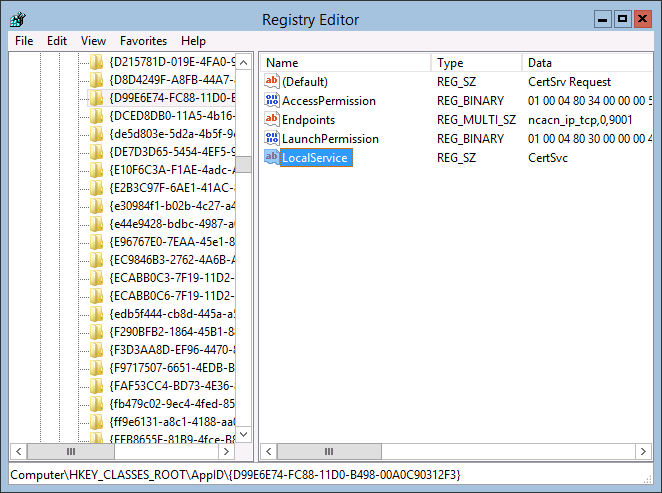
Normally this is done through the MMC Component Services Add-in. However, it is also possible to search within HKEY_CLASSES_ROOT\AppID\ for the CertSrv value since there is only one entry for it.
Configure Fixed Port
Create a new REG_MULTI_SZ value with Endpoints as name and a value of ncacn_ip_tcp,0,<port number> where <port number> can be replaced with an free port number of choice. In above screenshot I chose 9001.
More information on this registry key can be found in KB312960 and Enterprise Services (COM+) Security Considerations under the section “To configure a static endpoint for DCOM”
Restart Certificate Service
From PowerShell run Restart-Service CertSvc
To quickly verify that the configured static port is used run the following command: certutil -ping -config server.domain.com Monitoring network traffic to verify that the new port is used.